Role-Based Permissions in Inventory Systems: What’s Safe?
Understand how to design secure role-based permissions in inventory systems — including safe access levels, separation of duties, and built-in checks to prevent misuse.
Introduction
In a modern inventory management environment, multiple users — from administrators to technicians — interact with critical asset data daily.
Without proper access control, even a small mistake (or misuse) can result in data loss, inventory discrepancies, or unauthorized transactions.
Role-based permissions (RBAC) ensure that every action in your system aligns with a user’s responsibility — nothing more, nothing less.
TL;DR (for small IT teams)
If you’re tracking laptops and peripherals across people and locations:
- Keep most users read-only; give editing rights to 1–2 admins.
- Require approval for sensitive actions (delete, disposal, bulk edits, exports).
- Make sure every change has who/when/what history so audits are painless.
Start here:
- Small IT Teams overview: Asset tracking built for small IT teams
- Verification workflow: IT Asset Audit Checklist (for Small IT Teams)
- Hub: IT Asset Management Hub
1. Why Role-Based Access Matters
Inventory systems manage valuable and sensitive data: purchase details, asset IDs, vendor records, audit logs, and user history.
Improper access leads to:
- Unauthorized edits or deletions
- Manipulated quantities or asset status
- Audit trails broken by privilege misuse
- Loss of accountability
Role-based access control (RBAC) minimizes these risks by defining who can do what, and enforcing checks and balances throughout the workflow.
If you’re designing RBAC specifically for audit readiness, this walkthrough shows what auditors expect from ownership, traceability, and controls: How to Prepare for a Compliance Audit with a Digital Asset System.
2. Core Principles of RBAC in Inventory Systems
| Principle | Description |
|---|---|
| Least Privilege | Users get only the permissions necessary to perform their duties. |
| Separation of Duties (SoD) | No single user controls both asset creation and approval. |
| Granular Access Control | Permissions apply per action (view, edit, approve, delete). |
| Auditability | Every change is logged with user identity and timestamp. |
These principles build resilience against human error, fraud, and policy violations.
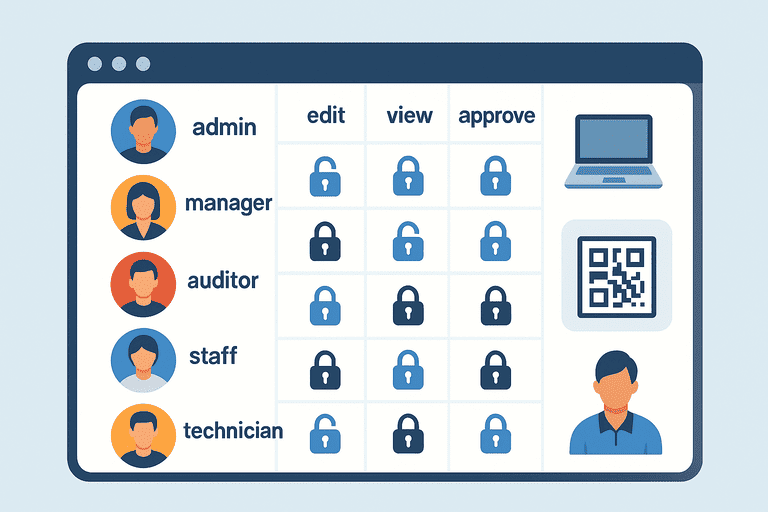
3. Common Roles in Inventory Systems
Below is a sample structure for secure and scalable access design:
1. System Administrator
- Full access to settings, roles, and integrations
- Can manage user accounts and system-level configurations
- Should not handle day-to-day transactions
2. Inventory Manager
- Oversees asset records, categories, and audit schedules
- Approves new asset entries or transfers
- Can generate and export reports
3. Department Manager
- Manages assets within their department
- Can assign and unassign equipment to employees
- Cannot modify system-wide configurations
4. Auditor / Compliance Officer
- Read-only access to all assets and logs
- Can run audit reports and flag discrepancies
- Cannot modify records
5. Employee / General User
- Can check out assigned equipment
- View assigned assets and return history
- Cannot edit or delete records
This separation maintains accountability and prevents privilege escalation.
4. Safe Role Design Checklist
When setting up user roles, consider this checklist to ensure compliance and safety:
| Control | Description | Why It Matters |
|---|---|---|
| ✅ Role Templates | Define reusable templates (Admin, Auditor, Staff) | Avoid inconsistent access |
| ✅ Approval Flows | Require manager validation for sensitive changes | Adds dual control |
| ✅ Access Reviews | Audit user permissions quarterly | Detect privilege creep |
| ✅ Conditional Access | Block edits outside business hours or from unknown IPs | Reduces risk exposure |
| ✅ Activity Logs | Record all user actions with timestamps | Supports traceability |
| ✅ Role Expiry | Auto-expire temporary access (e.g., for contractors) | Prevents dormant accounts |
5. Separation of Duties in Action
Let’s look at a common risk: asset disposal.
Without separation of duties, a single employee could both mark an asset as “disposed” and approve it — effectively removing it without oversight.
By splitting roles:
- Technician marks item for disposal
- Manager reviews and approves the request
- Auditor verifies the record in the next cycle
This layered verification prevents fraudulent removals and errors.
6. Granular Permission Examples
Modern inventory systems can apply fine-grained permissions like:
- Asset-level visibility (view only assigned assets)
- Action-level control (edit condition but not category)
- Location-based access (branch or department scope)
- Time-bound access (temporary contractors or projects)
These controls are especially vital in multi-tenant or hybrid work environments, where multiple teams share infrastructure.
For a practical example of where permissions tend to break down (approving moves, validating receipts, and updating locations across sites), see: Multi-Location Asset Transfers: Processes That Scale.
7. Implementing Checks and Alerts
Even with RBAC, continuous monitoring is key.
Smart checks can include:
- Automatic alerts for unusual activity (e.g., mass deletions)
- Change approval workflows for high-value assets
- Email notifications for role changes
- Reports on unused or dormant accounts
These safeguard your system from both internal and external threats.
To ensure alerts lead to action (instead of being ignored), implement escalation rules and owners: Inventory Notifications and Escalation Workflows.
8. Best Practices for Secure Role Management
- Document Role Responsibilities — publish an internal matrix describing what each role can do.
- Use Role Hierarchies Wisely — higher roles should inherit only relevant permissions.
- Apply the “Two-Person Rule” for critical actions like exports or deletions.
- Review Roles Regularly — update permissions as teams evolve.
- Simulate Permissions in Sandbox — test before deployment.
FAQ
What roles does a small IT team actually need?
Most teams can start with: Admin (1–2 people), IT Staff (limited edit), Manager/Approver (can approve sensitive actions), and Auditor (read-only). Keep it simple, then add roles only when a specific failure forces it.
Should employees be able to edit asset records?
Usually no. Let employees view assigned assets (and maybe request changes), but keep edits and assignments controlled. The best time to allow edits is when you can trust history and audits: IT Asset Audit Checklist (for Small IT Teams).
How often should we review permissions?
Quarterly is a good default, and immediately after org changes (new admins, layoffs, M&A). The cost of “privilege creep” shows up during audits and incidents.
What should be logged for audit readiness?
At minimum: who changed what, when, and from/to values (assignment, location, status). If your system can’t answer “who had it last?”, audits become guesswork.
Conclusion
Role-based permissions are not just an IT feature — they’re a security framework that protects your inventory integrity, reduces risks, and enforces accountability.
A safe and well-designed access structure ensures that your data remains reliable, compliant, and ready for audits — without slowing down operations.
Related reading
- IT Asset Audit Checklist (for Small IT Teams)
- Asset tracking built for small IT teams
- IT Asset Management Hub
- Why Shared Inventory Fails Without Accountability (and How to Fix It)
- Reducing Shrinkage and Loss with Smart Inventory Tools
- How to Run a Cycle Count Program for Shared Resources
- Risk Management in Asset Tracking — From Theft to Data Breaches
- Inventory Audit Checklist: What to Verify and How Often
Try InvyMate
Start tracking assets with QR codes and scheduled audits.